Computers with embedded readers will try to pass the SIM card as an RFID card. This happens because of their close proximity to each other within the device itself and can cause a number of odd, inappropriate behaviors by the MFA software. Some of these behaviors can look like:
- Computer beeping as if a card has been scanned at login
- The same username appears to attempt to "badge-in" every time
- Users frequently receive "This card is not registered" when that user is known to be enrolled
- The same username appears on multiple computers that they have never touched
- The computer beeps as if a card has been read then locks itself
- Being unable to enroll a contactless card; seeing a value appear in the card data during an enrollment before you even scan your card
The following instructions will demonstrate an example on how to confirm the behavior, followed by creating a RapidIdentity MFA-specific registry value that tells the software to ignore the smart card reader. These steps cannot be generalized into a single .REG file as the computers' UICC values will are unique to each computer.
Validating The Behavior
-
Open the Rapid Identity MFA desktop application.
-
Once open, click on Enrollment Wizard at the bottom.
-
Select the Proximity Card option.
-
The "Serial Number" will quickly populate with a long, overflowing string of hexadecimal values.
⚠️ Do not finish the card enrollment process at this step.Be sure to take note of the user assigned to this value. They will need to re-enroll their proximity card after this fix because their card was assigned to the SIM card value. You will also need to be sure and clear the client computer's cached credentials (and any others that might have experienced this or been affected by) by following the manual removal instructions or downloading our User Removal Tool.
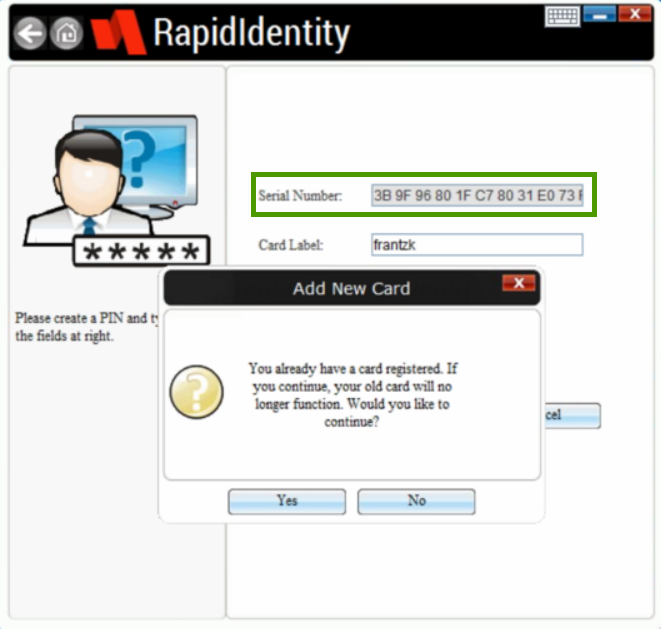
-
Open an elevated command prompt.
-
Run the command: certutil -scinfo
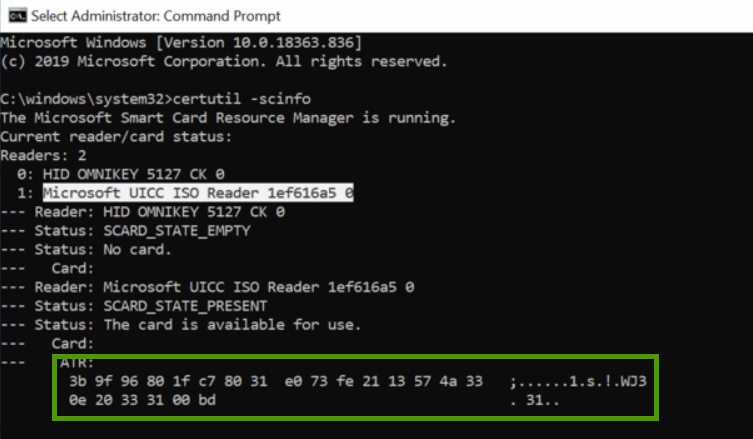
You'll notice that the hex value from Step 3 will appear under one of your computer's readers - typically the Microsoft UICC ISO Reader. This reader is your computer's unique smart card reader value that our software will need instruction to ignore.
Method 1 (Manually) - Ignoring The Reader
-
Copy the reader name (including the single number at the end of the string, in this example it's the zero).
-
Open your regedit and navigate to HKLM\Software\Foray.
-
Create a new multi-string sub-key:
"SCIgnoreReaders" MULTI_SZ = <card reader name from Step 1>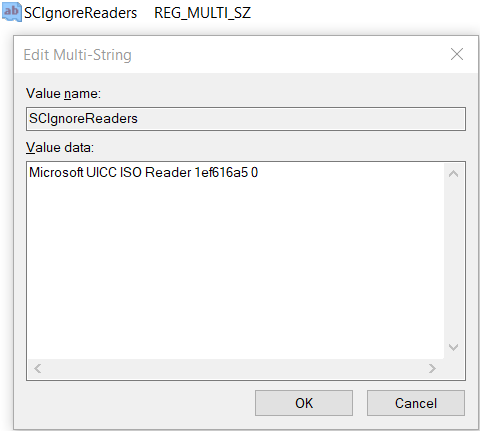
- Restart the computer.
Method 2 (Automated) - PowerShell Script
The following PowerShell script can be run to automatically perform the same actions as the method above, and will account for all UICC values that may be present on your computer(s). Copy/paste the code below. If you receive any errors when running, be sure you are running with elevated rights.
###########################
## SCIgnoreReaders Script #
###########################
clear
Start-Sleep -Seconds 2
Write-Output "Unrestricting ExecutionPolicy...`n"
Set-ExecutionPolicy -Scope LocalMachine -ExecutionPolicy unrestricted -Force
# Define registry paths
$regkey = "Device"
$registryBasePath = 'HKLM:\\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Calais\Readers\'
$readers = Get-ChildItem -Path $registryBasePath | Where-Object { $_.Name -like "*Microsoft UICC ISO Reader*" }
# Check if any Microsoft UICC readers exist
If ($readers.Count -eq 0) {
Start-Sleep -Seconds 2
Write-Output "Checking for UICC readers...`n"
Start-Sleep -Seconds 2
Write-Output "No readers found. Machine is not affected by SCIgnoreReaders issue.`nExiting..."
Start-Sleep -Seconds 3
Exit
} Else {
Write-Output "Readers found. Adding SCIgnoreReaders key...`n"
# Collect all reader names
$readerNames = $readers | ForEach-Object { $_.PSChildName }
# Define Foray registry path
$newpath = "HKLM:\\SOFTWARE\Foray"
# Create or update the SCIgnoreReaders reg key in HKLM\Software\Foray
New-ItemProperty -Path $newpath -PropertyType MultiString -Name "SCIgnoreReaders" -Value $readerNames -Force | Out-Null
# Disable each reader in the Microsoft Cryptography Readers registry path
foreach ($reader in $readerNames) {
$otherpath = "HKLM:\\SOFTWARE\Microsoft\Cryptography\Calais\Readers\$reader"
$groupvalue = "SCardDisabled"
New-ItemProperty -Path $otherpath -PropertyType MultiString -Name "Groups" -Value $groupvalue -Force | Out-Null
Write-Output "SCIgnoreReaders Registry Key Added: $reader"
}
}
Write-Output "`nResetting ExecutionPolicy...`n"
Set-ExecutionPolicy -Scope LocalMachine -ExecutionPolicy restricted -Force
$ExPo = Get-ExecutionPolicy
Start-Sleep -Seconds 2
Write-Output "Checking the reset...`n"
Start-Sleep -Seconds 2
If ($ExPo -eq 'Restricted') {
Write-Output "ExecutionPolicy: $ExPo.`n`nThe script ran successfully!`n"
Start-Sleep -Seconds 2
Write-Output "Closing PowerShell in 5 seconds..."
Start-Sleep -Seconds 5
Exit
} Else {
Write-Output "Something didn't work quite right. Please check the execution policy again.`n"
Write-Output "Current ExecutionPolicy: $ExPo"
}
