Windows Setup
-
Check that the Network Policy Server is on.
-
Configure the RADIUS Client.
-
Configure the Connection Request Policy.
-
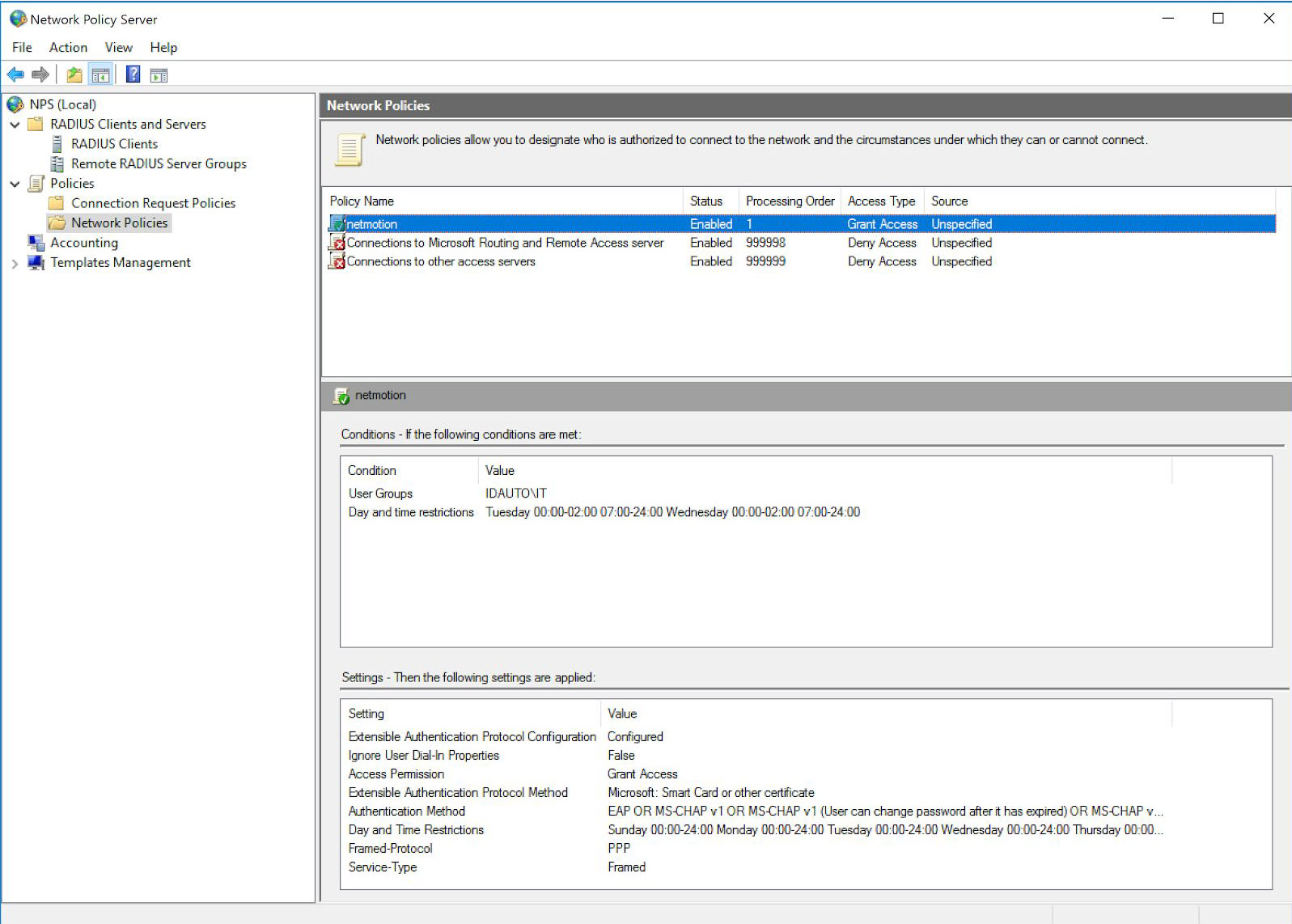
Configure the Network Policy.
RapidIdentity MFA Software Setup
-
Enable the RADIUS.bat by running the following in an elevated command prompt:
cd "C:\Program Files\2FA\ONE Server\tools" && .\Enable_2FA_RADIUS.bat -
Note
By default, the NPS server does not have logging enabled. You will have to enable this logging either through the NPS GUI or with the following CLI command (as an Administrator):
auditpol /set /subcategory:"Network Policy Server" /success:enable /failure:enable -
Restart the NPS Server.
MFA-Specific RADIUS Settings
If desired, specific RI MFA registry settings can be configured for different connection policies within NPS.
-
In the MFA Server's Registry Editor, expand and navigate to:
HKLM\Software\Identity Automation\RapidIdentity MFA -
If it does not exist already, create a new key under RapidIdentity MFA named "RADIUS".
-
Under the RADIUS key, create a new key and name it the same as the Connection Request Policy in your NPS, exactly as it appears, to which these settings should apply.
-
Add the values that fit your organization's needs using the table of available values below.
RADIUS Registry Settings
These policy-specific settings will override any values configured in the default “RADIUS” key.
| Value Name | Value Type | Value | Description |
|---|---|---|---|
| AllowPassthroughIfPushNotConfigured | DWORD | 0 (Disabled) 1 (Enabled) |
Allows for validation to continue if the user does not have PingMe configured yet. |
| AllowPassThroughOfNon2FAUsers | DWORD | 0 (Disabled) 1 (Enabled) |
Allows RADIUS authentication to hand-off to Active Directory to validate users that are not currently in RapidIdentityServer. This is useful for migrations or supporting different requirements from different user groups. |
| ForcePAP | DWORD | 0 (Disabled) 1 (Enabled) |
Forces RapidIdentity Server to use strict PAP protocol as opposed to MS-CHAPv2 or EAP protocols in order to communicate with some third-party vendors that may not be able to support those protocols. |
| InstallPath | STRING | Install path of the website. For example, C:\Program Files\2FA\Web Site Name |
By default, this setting will be created if the system is only hosting one website using RADIUS. If there are multiple web sites with RADIUS, create a new key under the RADIUS key. Ensure the name matches the NPS Connection Policy name. If it does not, then RapidIdentity Server applies the default settings under the RADIUS registry key. |
| LogLevel | DWORD | 0 (Disabled) 1 (Enabled) |
Generates a log file to reference for RADIUS troubleshooting. Create the logs folder in order for the logs to start generating in the location C:\Logs. |
| ReAuthInterval | DWORD | Integer (seconds) | Allows for third party vendors leveraging RADIUS that may replay the same authentication event in a legitimate manner (such as for load balancing). Recommend intervals are 3 or 5 seconds. |
| RequirePushLoginAdditional | DWORD | 0 (Disabled) 1 (Enabled) |
This will add a PingMe validation after the password is validated. |
| RequirePushLoginOnly | DWORD | 0 (Disabled) 1 (Enabled) |
This will skip password validation and perform only a PingMe validation. |
| RequirePushLoginOnlyIfAvailable | DWORD | 0 (Disabled) 1 (Enabled) |
This will check to see if they user has PingMe configured. If so, RapidIdentity Server sends a request to the registered device for that user. |
| WebsiteURL | STRING | http(s)://FQDN/one | This is a string value and should point to the default RapidIdentity Server website and it assumes that http://localhost/one will work. This registry setting will inform NPS how to find the correct website. |
If most NPS connections use MSChapV2 or some other protocol to communicate, but one specific connection policy in NPS (e.g. PapConnPolicy) required PAP as a protocol, a registry key could be created called “HKEY_LOCAL_MACHINE\SOFTWARE\2FA TECHNOLOGY\ONE SERVER \RADIUS\PapConnPolicy”, create a DWORD value named “ForcePAP”, and set it to 1 (as described below). In this way, all other connection policies would use the default protocol to communicate, but when an NPS (RADIUS) request comes in via the PapConnPolicy connection policy, it will use PAP.
