RapidIdentity does not need to communicate directly with any respective domain controller to keep updates with users' passwords. The RapidIdentity desktop client instead listens to official domain authentication requests during normal use. RapidIdentity can tell when a password is valid by how AD responds. Once a valid password is detected and verified by an AD response to an official authentication request against AD or your local machine, the password is then encrypted and stored—encrypted and salted—in the ONE database for future reference. The password is stored so that even outside of your Active Directory-managed network, users may still authenticate to RapidIdentity services by leveraging the Windows AD Password or Windows AD Password as PIN methods in an environment where your domain controller might be unreachable.
Setup
Authentication Set
In order for the AD password to update through our application, the user has to have the AD authentication method included as a Primary Authentication Method in the user's current RapidIdentity Authentication Set. If AD is not listed, the user will not be allowed to update their password through the desktop client: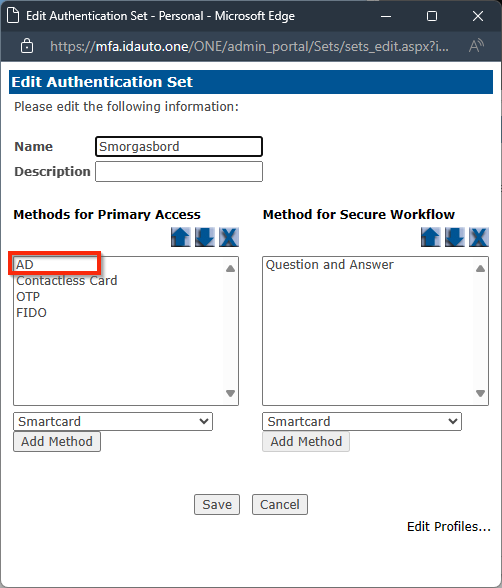
MFA Policy
By default, the MFA clients are able to update the AD password from the client. In the MFA policies under the Logon tile, you can control this ability by setting the option to Enabled or Disabled.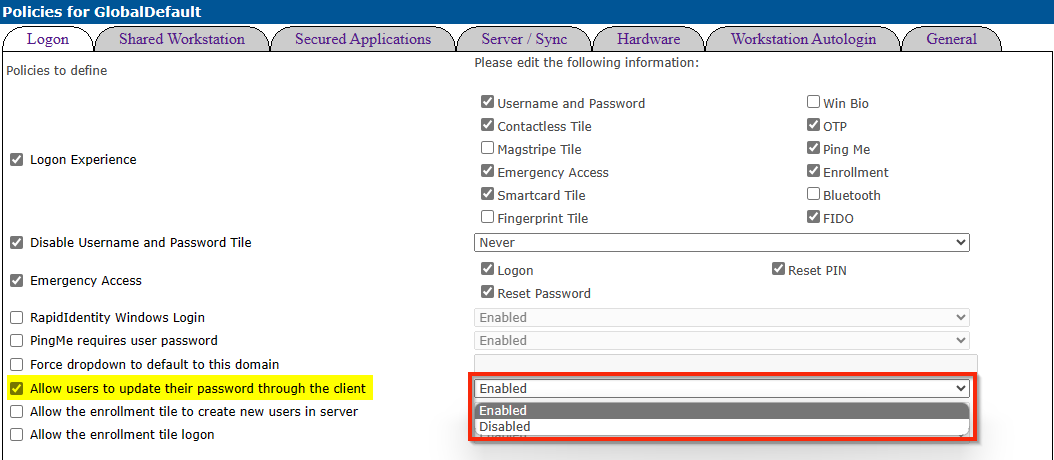
Method 1 - Update AD Password Through Desktop Client
- Open the desktop application.
- On the left-hand side, click the Password button.
.png)
- A pop-up will appear. Select any one of the available authentication methods to prove your identity.
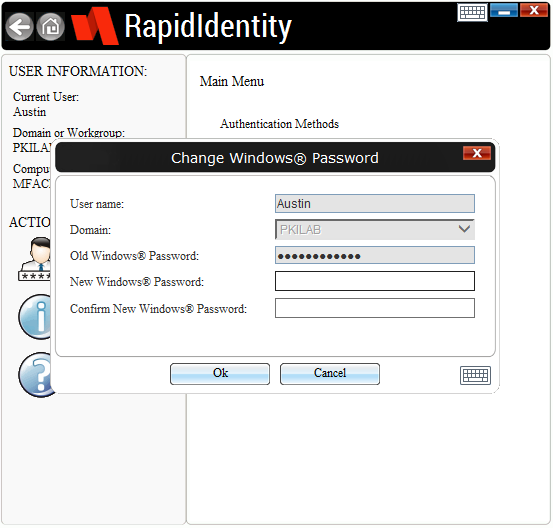
- In the new window, enter/confirm your new password. Click Ok when you are done.
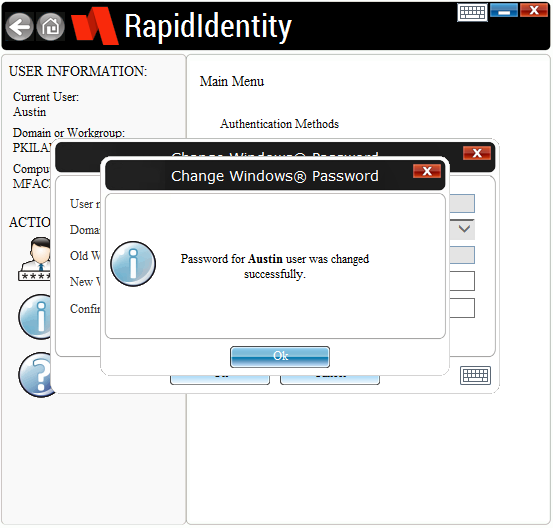
- You should receive one final window that your change was made successfully.
Method 2 - Update Password Outside of RI
When a password is updated outside of RapidIdentity, either through Active Directory or the Change Password option (when using Ctrl+Alt+Del), RapidIdentity will discover this mismatch at the next login. It will then prompt the user to update their password with RapidIdentity with their new AD password.
- Log in with a valid authentication method.
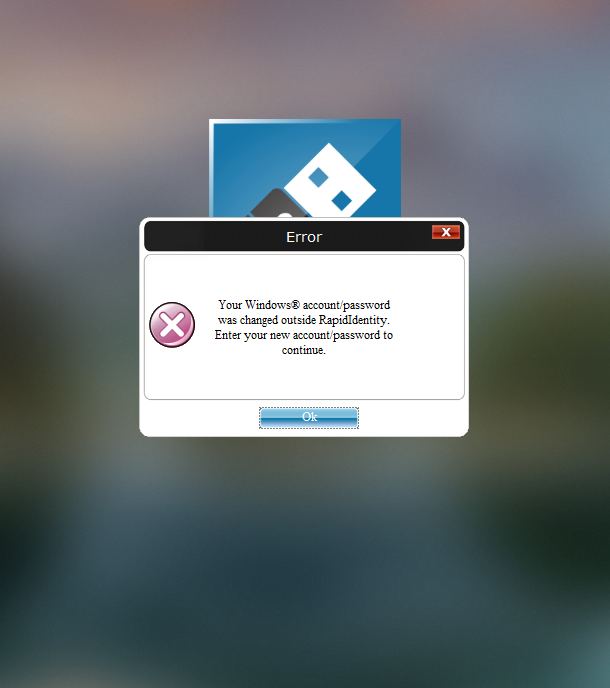
- You will receive a pop-up that your password was changed "outside of RapidIdentity". Click Ok.
- At the next window, type in your new password.
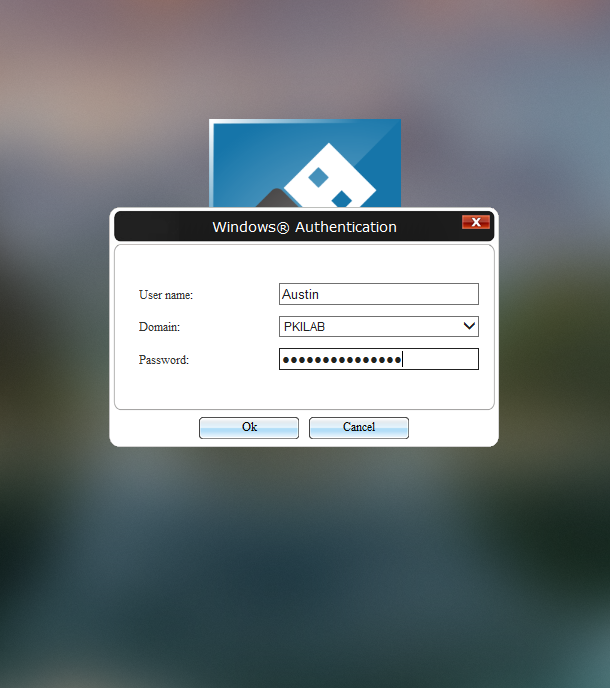
- When finished, click Ok. You will then be logged into your account, and RapidIdentity will now be aware of the new password and in sync with your AD environment again.
Troubleshooting
RapidIdentity assumes you will have one of the following scenarios met to keep passwords in sync and up to date with the domain controllers.
Scenario 1 includes intermittent, periodic updates from bringing your machine in and out of the Active Directory managed network either via VPN or physical presence. Once inside the AD-managed network, the local RapidIdentity cached account will function very much like a Windows Active Directory cached account. The machine will sync with the AD server and become aware of any changes that happened during the machine's time outside of the managed network. If a password update occurred, the end user would be alerted that a change has occurred outside of RapidIdentity and prompt the user for the updated password.
Scenario 2 includes an Always On VPN solution like NetMotion/Absolute's Unattended Mode or Cisco AnyConnect's "Start Before Login" functionality. These methods rely on certificate-based authentication instead of user-based authentication. The benefit of the Always On VPN solution is the ability to communicate to the domain controller before Windows Login.
If you are experiencing password synchronization issues, see if you are able to run a GPUpdate from the command prompt, on the client, to verify you are able to see the domain controller. If the GPUpdate fails, try reconnecting with your VPN and attempting the GPUpdate again. Once you are able to run the GPUpdate command successfully, exit and re-open the RapidIdentity Desktop Client to see if you are prompted to update your Windows password because it was updated outside of RapidIdentity.
Lockout Before VPN Connection:
Domain password policies are NOT enforced for cached domain accounts that reside on machines that are currently outside of the managed Active Directory network's visibility by default. To unlock a domain account that has been locked at the Windows account level, you will have to make contact with the domain controller. This can be accomplished by logging into another valid cached domain account that has not been locked out or by signing in with a machine local account to reconnect your VPN to make contact with your domain controller. The best recommended solution is to make contact with your domain network via VPN or physical presence.
We are unable to unlock RapidIdentity MFA accounts remotely via the Web Admin Portal. If a cached domain account that currently resides outside of the managed domain network gets locked out, there is nothing RapidIdentity can do currently to override your domain's policy and unlock the Windows account remotely. For this reason, we suggest leveraging an Always On type of VPN solution that connects before user authentication.