This article covers the basics of RADIUS integration troubleshooting with the RapidIdentity MFA software. These are the first things to check and try. If RADIUS authentications are still failing after these suggestions, please reach out to our Support team for more assistance.
The file paths used in this article are under the assumption that your MFA server is on v4.9.5.1 or later. If it is not, it is strongly recommended to upgrade. Please see our server upgrade information page for more information.
NPS Logs Not Appearing In Event Viewer
Network Policy Server logs are important to gather or read when dealing with RADIUS and VPNs. Most of the time, these logs will be enabled, but every once in a while, they might not be. These steps help enable them via the command line.
- Open an elevated command prompt on the server where NPS is installed.
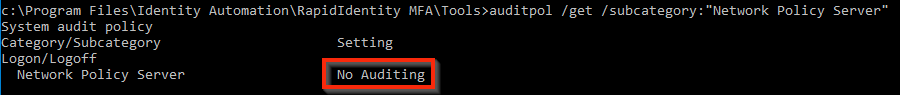
- The following command can be run to confirm that the NPS logs running status:
auditpol /get /subcategory:"Network Policy Server"
In this example, they are not currently running:
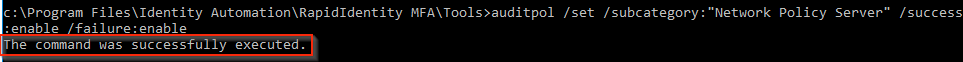
- Type the following command to enable both success and failure messages:
auditpol /set /subcategory:"Network Policy Server" /success:enable /failure:enable
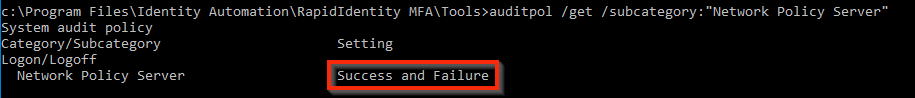
If you run the same command from Step 2, you should see that they are now running:
Authentication Failure | Event 6273 & Reason Code: 21
These are the most common error(s) that we have come across in Windows Event Viewer NPS Logs. If your RADIUS and/or VPN setup is used in conjunction with RapidIdentity MFA (like using PingMe/OTP to log IN to your VPN), and this is the frequent error message received, it is likely an issue with our .dll.*
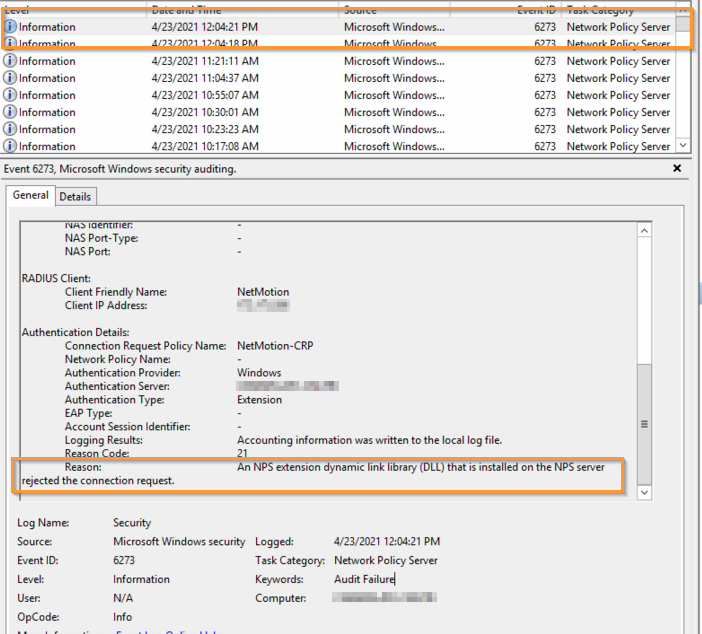
Typically, this is caused by MFA server upgrades (v4946 or lower => v4951 or higher) or files being moved, making the file path of the .dll unknown to the registry key.
- Open your Registry Editor.
- Navigate to: *HKLM\System\CurrentControlSet\Services\AuthSrv\Parameters*
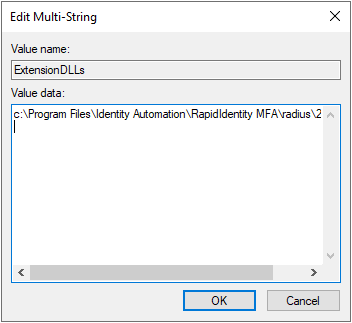
- There will be a REG_MULTI_SZ key call ExtensionDLLs. It may have one or multiple values - path(s) to the 2FANPS.dll. Update the value so that there is only the one path:
C:\Program Files\Identity Automation\RapidIdentity MFA\radius\2fanps.dll
Be sure the path is correspondent to your MFA server version. You can verify that the path and that the file is there by checking for the \RADIUS folder in the install path.
RADIUS Batch File
This will register or re-register the 2FA Radius.dll and ensure the policies are validating credentials against the database. This file needs to be run after any server upgrade, especially an MFA server upgrade, and may need to be run after a reboot if NPS does not start properly.
Before Executing Batch File
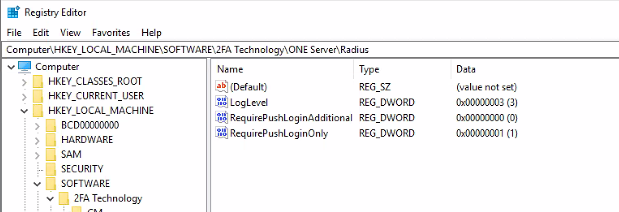
- In your Registry Editor, go to:
HKEY_LOCAL_MACHINE\SOFTWARE\Identity Automation\RapidIdentity MFA
- If you have another key/folder called "\RADIUS" that extends the path in Step 1, take a backup or screenshot of the keys and values inside.
Executing The Batch File
- Open an elevated command prompt.
- Navigate to: C:\Program Files\Identity Automation\RapidIdentity MFA\tools
- Type:
Enable_2FA_RADIUS.bat
- Press the Enter.
